Our Cybersecurity Advisory Services, part of our Cyber Security Portfolio, include plan, build, run capabilities that assess and strengthen cybersecurity posture to safeguard brand reputation, business processes and regulatory compliance with cost-optimized security controls. Our System Integration and Managed Security Services, defend business operations and enhance cyber resilience across clouds, networks, perimeters, endpoints, identities, data and apps. These integrated solutions and managed services increase business agility and secure the modern enterprise. Geared by world class partners, EBS is poised with any industry to provide security solutions that can give them assurance to the highest level.

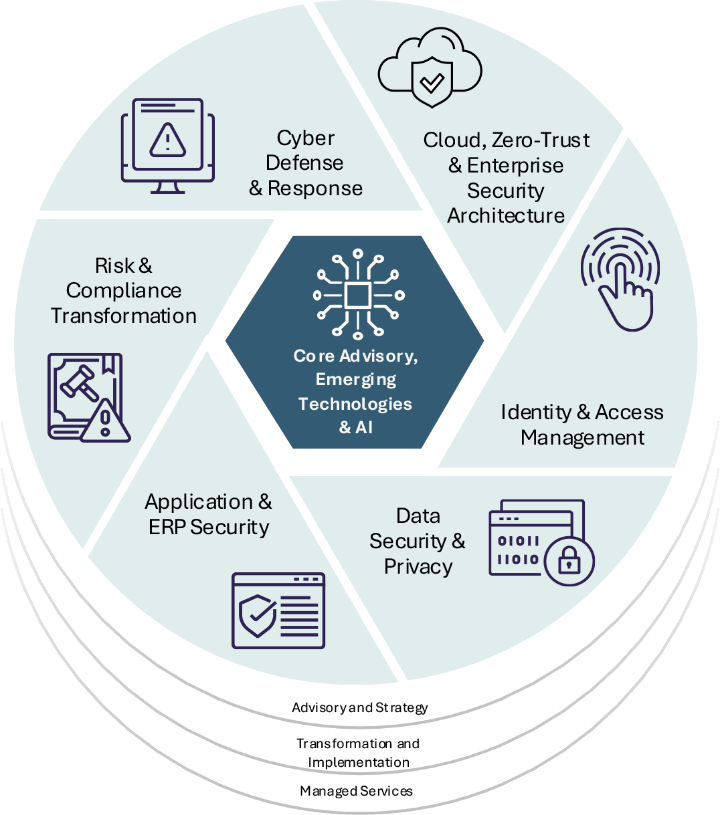
Core Advisory
We secure the modern enterprise through a strategy-first, business-aligned approach
Emerging Technologies & AI
Wipro’s Artificial Intelligence, Open Source, 5G, and more
Risk & Compliance Transformation
Helping C-suite assess and enhance the enterprise cybersecurity risk posture, adhere
Cloud, Zero-Trust & Enterprise Security Architecture
Fortify defenses both on cloud and data center against the most advanced cyber threats
Identity & Access Management
Next-gen Identity & Access Services to secure your digital transformation journey
Data Security & Privacy
Safeguard your most valuable assets with comprehensive data and OT/IoT security solutions tailored to your needs.
Cyber Defense and Response
Seamless and cost-effective management of security operations provided in an as-a-service model.
| Domain | Product Type | Vendor Name | Product Name | Best industry match & Strength of references (see legend below) | |||||
| Financial Services | eCommerce & Retail | Telco, Media & Technology | Utilities, OEM’s & Production Industry | Public Services, Institutions & Law | Airline, Transport & Logistics | ||||
| Information Security (Data Mgmt. & Security) | – | – | – | – | – | – | – | – | – |
| Information Security (Data Mgmt. & Security) | Secure DB Logging | Veriskop | Caplan | ««« | «« | ««« | « | « | «« |
| Information Security (Data Mgmt. & Security) | Test Data Mgmt. with Static Data Masking | Veriskop | CopyCat | ««« | «« | ««« | « | « | «« |
| Information Security (Data Mgmt. & Security) | Web-Based SQL Editor | Veriskop | DDR | ««« | «« | ««« | « | « | «« |
| Information Security (Data Mgmt. & Security) | Dynamic Data Masking | Veriskop | CopyCat Live | ««« | «« | ««« | « | « | «« |
| Information Security (Data Mgmt. & Security) | Dynamic Data Access | Veriskop | DDA | ««« | «« | ««« | « | « | «« |
| Information Security (Data Mgmt. & Security) | Sensitive Data Discovery | Veriskop | SDD | ««« | «« | ««« | « | « | «« |
| IT Monitoring & Cyber Security | – | – | – | – | – | – | – | – | – |
| IT Monitoring & Cyber Security | PAM Platform | Krontech | Single Connect | «« | « | ««« | « | «« | « |
| IT Monitoring & Cyber Security | Soft OTP | Enqura | EnSecure | ««« | «« | «« | – | – | – |
| IT Monitoring & Cyber Security | IAM | Monofor | Monosign | ««« | «« | «« | « | « | «« |
| IT Monitoring & Cyber Security | SAST Testing & Training | Attackflow | Attackflow Cyberchallenge | ««« | «« | «« | « | ««« | « |
| IT Monitoring & Cyber Security | Security platform for endpoint, SW asset & inventory mgmt. | Çekino | Gardyan | ««« | «« | «« | « | ««« | « |
| IT Monitoring & Cyber Security | Cyber Security Training for SOC | Cyber Struggle | Aegis / Alpha / Ranger (Certifications) | ««« | «« | «« | « | « | ««« |
| IT Monitoring & Cyber Security | Crowd-sourced Pen. Testing | Bug Bounter | – | ««« | « | ««« | «« | «« | ««« |
| IT Monitoring & Cyber Security | PCI & SWIFT Certification | Secure Way | – | ««« | «« | « | «« | « | ««« |
| ««« | Dominant: best match by design and reference | |||
| «« | Strong: good match by design, with high potential in that industry | |||
| « | Challenger: applicable use cases but yet to get attention in that industry | |||
| – | Not applicable for that industry | |||


